Yesterday I tried to delineate four different kinds of governmental attacks on the internet — those by illegitimate regimes trying to protect themselves, those mounted in the name of national security, those mounted by or at the behest of powerful gatekeepers to protect old business models, and those aimed at cultural engineering. The purpose was not classification for its own (rather exhausting) sake but to enable us to think more clearly about the nature of the what governments are trying to do to us. From it we can start to develop a spectrum of different types of attack.
The spectrum I have in mind has at one end cultural engineering. Attacks mounted in pursuit of cultural engineering — blocking gambling and pornography sites, for example — are essentially political in nature. There are driven by politicians aiming to cultivate influential groups such as conservative religious groups or impose their own interventionist social views on internet users.
Next to cultural engineering on the spectrum are attacks mounted by or on behalf of influential gatekeepers. They are driven by the interests of powerful stakeholders able to influence policy makers in preserving pre-digital sources of revenue or authority — think the copyright industry.
In both cases, their attacks are based on a misapprehension that the internet is a medium just like traditional mainstream media and can and should be regulated like traditional media. The mainstream media has, much more strongly than most sectors, been regulated by gatekeepers protecting legacy business models, as Tim Wu’s Master Switch and the history of Australian communications policy shows.
Indeed, the convergence review that is currently under way in Australia is likely to be used by some as a mechanism to further extend mainstream media regulation to online media in the name of regulatory uniformity.
As I’ve repeatedly argued, the internet is fundamentally different from traditional media because the platforms, the applications, are not what’s important, but the facilitation of interconnectedness. The internet is not another form of passively receiving news and entertainment, but a plugging-in of the users to other people, an abolition of geography to enable the establishment across the globe of the type of communities that hitherto existed only in geographically specific areas — ones characterised by deep bonds of interest, civic mindedness and information sharing.
In short, attacks based on gatekeeper influence and cultural engineering exemplify the longstanding internet cliché — they Don’t Get It.
Gatekeeper and cultural engineering attacks also tend to be peripheral to core government business (they’re often driven by culture or communications ministers) because they’re primarily about regulating social behaviour and propping up business models or modes of power under threat from the internet. The key driver is how influential the gatekeeper or moraliser is — in Australia’s case, the copyright industry, the legal industry and broadcasters are powerful enough (the copyright industry is powerful the world over, because of its sheer size and its grip on the US governmental apparatus); religious fundamentalists are somewhat less powerful, and retailers nowhere near powerful enough, as we’ve seen in recent months.
But attacks by the most powerful gatekeepers — the legal industry and the copyright industry, are further along a spectrum of effectiveness than mere cultural engineering. They’re closer to the other end of the spectrum, attacks driven by national security and regime survival.
This is not to downplay the serious of some gatekeeper attacks — people are getting jailed for links to file-sharing sites, for example — but to note that they often lack the concerted effort of state apparatus that would make them truly effective, because they’re not core government business — such as national security and regime survival.
Perhaps we have a spectrum of attacks that look like this?
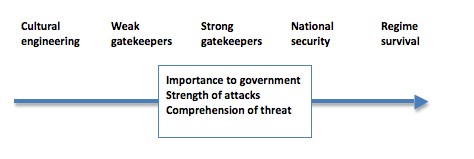
Attacks at the right-hand side are core government business — at least as perceived by its members — and do understand the nature of the internet and the threat of interconnectedness. The defence, security and intelligence sectors of government Get It, and aim at either preventing altogether, or neutering the impact of, their citizens linking up and communicating about government activities.
And regimes hell bent on preserving power will stop up at nothing — right up to killing bloggers and switching off the internet — to save themselves. Some may cavil at locating the actions of democratic governments on the same spectrum as those of China or Iran, but this isn’t a moral spectrum, it’s about what governments are trying to do and how determined they are to do it.
The suggested spectrum might be useful in keeping a sense of proportion about governmental attacks on the internet. Many gatekeeper or cultural engineering attacks are ineffectual — because they fundamentally misunderstand what they confront — or can be defended against successfully on free speech grounds. Laws against online gambling in Australia and the US are a dead letter.
Stephen Conroy’s internet filter will be easily circumvented by anyone with some basic IT know-how. File-sharing continues to grow. Judges can froth at the mouth about Twitter but there will always be people outside their jurisdiction ready to break injunctions — national borders are an important impediment to effective enforcement of cultural engineering and gatekeeper attacks. But national security-sourced attacks are far more coordinated internationally, given they are conducted by agents already closely enmeshed with each other.
Robert McClelland illustrated this today when he stated, as part of an announcement of the government’s new cyber strategy, that the government was working on cyber security issues with the United Kingdom and United States.
In addition to not misunderstanding their target, attacks sourced from security establishments are also resourced seriously, and draw on existing government infrastructure. And in the case of national security-sourced attacks, they are not contested in the way that cultural engineering or even gatekeeper attacks are. Attempts to impose an internet filter, for example, spark significant debate over issues such as free speech. National security measures, however, tend to command greater acquiescence. The mainstream media falls silent and major political parties fall into line when men (and the occasional woman) in uniform speak about the need for security.
The growth in national security-sourced attacks partly reflects a catch-up by security agencies and governments more widely, who have had to adjust to new types of communication networks and new forms of threats; in Western countries (and particularly those, unlike the United States, with Westminster systems and independent bureaucracies) there is a far stronger emphasis on security agencies acting strictly within their legal frameworks, ensuring those frameworks must be updated to adapt to an online world. The Australian government’s intention to amend the act governing its domestic spying agency to enable it to pursue WikiLeaks is a clear example of this, since WikiLeaks doesn’t even fit within the broad ambit of “foreign power” targets intended to incorporate post-9/11 “non-state actors”.
And for that matter, who knows quite how NATO would define an amorphous, unorganised, self-identifying entity such as Anonymous, not so much a non-state actor as a non-actor actor, conjuring the entertaining image of NATO staff, with experience of dealing with enemies fuelled by Soviet communism, Balkan nationalism and al-Qaeda’s Islamofascism trying to understand the geo-political strategy of “bringing the lulz”.
But it is more than just catch-up, because a new threat has emerged along with interconnectedness. The abolition of geography isn’t the only achievement of the internet. It has abolished paper. Information is no longer confined to a format weighing 80 grams per square metre. Information that would have taken weeks or months in the analog era to copy and distribute (think Ellsberg’s Pentagon Papers) can be sent to millions of people in a second. Since information control is a key component of national security, protecting dictatorial regimes and preventing the embarrassment of either democratic or dictatorial governments, this is a serious, almost existential threat. Whistleblower sites — and WikiLeaks was only an innovation of the form — has been the crystallisation into reality of exactly the nightmare posed to governments by the internet. The biggest threat facing Western governments in the past decade hasn’t been Islamofascist terrorism but the rise of the internet, which threatens to undermine them in ways even successful suicide bombers never could.
Next week: what previous centuries tells us about attacking the internet, and what to do about it.








should all forms of intervention be considered as “threat”? something that’s bothered me for a while is that users of the internet appear nearly totally unaccountable when it comes to defamatory remarks. At its most basic, we’re talking about the classic “goss” – i.e. facebook gossip networks talking about which students have been sleeping their way through the school staff.
At its more predatory you have people posting photos to destroy reputations.
At its most sophisticated, a viral campaign promoting propaganda that is patently false and targeted at destroying the reputation of an individual, corporate entity or government.
Recently, I’ve observed a number of viral videos which present as funny digs at the piss-poor performance of certain companies, or just make outrageous claims which may or may not be true… it doesn’t really matter to the average user, they’re funny! They appear to be originating from ordinary people, but given the anonymity of the internet, there’s absolutely nothing stopping a PR acting on behalf of an industry competitor to systematically destroy the reputation of a company. Protections exist/have existed to restrict this kind of behaviour. But how do you link back the actions of several individuals or relatively anonymous operations to a particular company who is financing such a venture? The internet provides plenty of barriers preventing links to be made directly. And by the time some determined investigation found anything, the damage is done.
I’m not really sure what can be done to address this kind of thing and I forsee a time in the future where no amount of positive PR or advertising by a company will be enough to negate the impact of a well financed, well targeted negative PR attack from a cashed up industry incumbent.
As you point out, Simon, there are already laws against that sort of behavior. We just need to find ways of enforcing them.
Much of our struggle with the new technology comes down to finding ways of reconciling our expectations with what is actually viable. Your question mirrors what already exists outside the Internet: that PR and media will present biased and even wildly inaccurate views of situations affecting us. The Net just adds another layer of speed and camouflage.
It’s difficult, now, for people to retain their illusions about control of the world around them. The ordinary person suddenly finds out that the world is made up of lots of ordinary people, all with their views and varying levels of maturity. The person who has amassed power gradually finds out that s/he can’t control what people see and hear anymore.
We shouldn’t give in to fear, or let others manipulate us with it. The Net is an amazing opportunity for cooperation, creativity and convenience. We just need to adjust our legal frameworks and enforcement procedures to protect it, rather than strangling it.
“If you tell a lie big enough and keep repeating it, people will eventually come to believe it. The lie can be maintained only for such time as the State can shield the people from the political, economic and/or military consequences of the lie. It thus becomes vitally important for the State to use all of its powers to repress dissent, for the truth is the mortal enemy of the lie, and thus by extension, the truth is the greatest enemy of the State.”
Joseph Goebbels
It looks like the point made by the German Minister for Propaganda has been taken on board by governments generally.
Stephen Conroy is only following in the footsteps of Gareth Evans in his desire to censor the Internet. I expect that, given time and persistence, he will achieve his aim.
Bernard said: “The internet is not another form of passively receiving news and entertainment, but a plugging-in of the users to other people, an abolition of geography to enable the establishment across the globe of the type of communities that hitherto existed only in geographically specific areas — ones characterised by deep bonds of interest, civic mindedness and information sharing.”
And there in a nutshell is why we need the NBN. The only way to realise the potential encapsulated in Bernard’s paragraph is through synchronous, contention-free, noise-free data pipes which are not subject to reception issues. Fibre to the home.
Awesome series so far Bernard, thank you.